Question: Describe the meaning of each of the
Describe the meaning of each of the entity– relationship diagrams shown in Figure 14-17.
Figure 14-17:
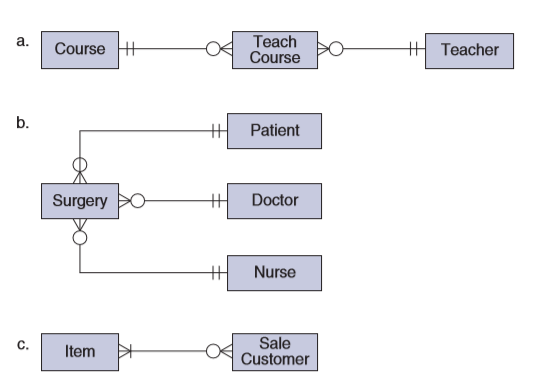
Transcribed Image Text:
Тeach Course a. Course + H Teacher b. H Patient Surgery + Doctor Nurse Sale Customer С. Item
> Go to the AICPA website at http://www.aicpa .org. What are the top 10 information technologies for the current year? How do these items compare with the list in Figure 3-1? Is it common for new items to appear, or do you think this list is “stable” from
> Design tables to store the following attributes (make sure that all tables are in third normal form). Student name, student phone, classes taken by student, student address, class number, class time, class room, students’ grades for each class.
> An advertisement for a desktop microcomputer says that it includes a 500-gigabyte hard drive. Exactly how many bytes is this?
> Which of the following holds the most data? a. 1 DVD disk b. 1 Hard disk (capacity: 500 gigabytes) c. 10 CD-ROMs
> Bennet National Bank’s credit card department issues a special credit card that permits credit card holders to withdraw funds from the bank’s ATMs at any time of the day or night. These machines are actually smart terminals connected to the bank’s centra
> Use your Internet browser and preferred search engine to find a company that provides financial and accounting outsourcing (FAO) services. What services does this company provide? Find a second company and compare its services with those of the first compan
> Design tables to store the following attributes (make sure that all tables are in third normal form): Customer name, customer address, customer phone, and names of customers’ children.
> As machine learning and artificial intelligence tools become more sophisticated, they are being adopted more and more for detecting fraudulent activity. Using your favorite search engine, find an example of a fraud or other white collar crime that was dete
> Do individuals engage in outsourcing? If you answered yes, give some examples.
> Literally thousands of business process management (BPM) solutions are available to help managers accomplish tasks in a more effective, efficient manner. Assume that you work in a payroll processing function and your supervisor asked you to select a BPM s
> An employee at Andrienne Hill Cosmetics believes that Access reports are a throwback to a former age when printed outputs were more common. Today, he said that they are no longer needed. Do you agree?
> Search the Web for unusual and interesting uses of RFID tags. Find at least two that are unusual and share those in class.
> Access 2016 now enables users to store calculated fields as normal fields in database tables. Do you think they should?
> What is an entity–relationship (E-R) diagram? What can you determine about an organization from examining an E-R diagram?
> What are database cardinalities? Give some examples of cardinalities for an accounting application other than sales.
> Backwater University is a small technical college that is located miles from the nearest town. As a result, most of the students who attend classes there also live in the resident dormitories and purchase one of three types of meal plans. The “Full Plan”
> Interview a sample of auditors from professional service firms in your area. Ask them whether or not they plan to offer any of the assurance services suggested by the AICPA. Also, find out if they offer services other than financial auditing and taxation. D
> Can you find an example (other than the one described in Case-in-Point 9.6) of a firm that is using lean production concepts that are supported by lean accounting? How are they doing?
> What are the four symbols used in data flow diagrams? What does each mean?
> Visit a local business or search online and collect some examples of source documents used in an AIS. For each source document you collect, discuss its purpose(s). Are different source documents required for manufacturing firms versus merchandising organi
> Flowcharting is both an art and a science. Guidelines can be used to make better flowcharts. What are these guidelines for document, system, and data flow diagram flowcharts?
> This chapter describes how to create tables and records in Microsoft Access. What other database management systems are available? Use the Internet to learn more about these systems.
> Take a survey of the students in your class to find out what jobs their parents hold .How many are employed in manufacturing? How many are employed in service industries? How many could be classified as knowledge workers?
> Choose three or four issues of one of these journals: Journal of Accountancy, Internal Auditor, Strategic Finance, and Management Accounting. Next, count the number of articles that are related to IT. In addition, make a list of the specific technology di
> What words were used to form each of the following acronyms? a. ABC b. AICPA c. AIS d. CFO e. CISA f. CITP g. CPA h. CPM i. ERP j. FASB k. HIPAA l. ISACA m. IT n. KPI o. SAR p. SEC q. SOX r. VAR s. XBRL
> Continuous auditing has the potential to reduce labor costs associated with auditing. It also can provide audit assurance closer to the occurrence of a transaction, which improves the reliability of frequent or real-time financial reports. Using an Intern
> Savage Motors sells and leases commercial automobiles, vans, and trucks to customers in southern California. Most of the company’s administrative staff work in the main office. The company has been in business for 35 year
> Information systems auditors sometimes use tools or information they can download from the Internet. These tools or information may include software, audit guides, or computer security advisories. Locate some examples from the Internet of audit tools, au
> Visit www.isaca.org, the website for the Information Systems Audit and Control Association. Investigate the Certified Information Systems Auditor (CISA) credential. Describe the purpose of the credential and the types of auditing CISAs perform.
> The Espy Company recently had an outside consulting firm perform an audit of its information systems department. One of the consultants identified some business risks and their probability of occurrence. Estimates of the potential losses and estimated cont
> Use the Customers table in the BSN database that accompanies this book and the Report Wiz-ard to create the report in Figure 16-14. Note that you will have to reformat and perhaps reposition several labels, and add both labels and a graphic in the header
> Using the Customers table in the BSN database that accompanies this book, and following the directions in this chapter, create the report in Figure 16-8. Note that you will have to reformat and perhaps reposition several labels, and add both labels and a
> If you have not done so already, use the Customers table in the BSN database that accompanies this book and the directions in this chapter to create the form in Figure 16-1. Make sure that you reformat the default positions of the various textboxes as sh
> Using the Customers table in the BSN database that accompanies this book, and following the directions in this chapter, create the form in Figure 16-1. Make sure that you reformat the default positions of the various textboxes as shown in the ï¬
> Provide a short explanation of the difference between each of the following sets of terms: a. bound control versus unbound control b. design mode versus run mode c. ◀ symbol versus ▶ symbol on a form’s navigation bar d. form versus subform e. normal data
> A database report has seven major sections. a. Identify each one and provide a short explanation of each section. b. Identify a report that a database application might generate, and indicate what data might be found in each section of the report for you
> A form’s navigation bar has five symbols on it. Identify each one and indicate its use.
> Barra Concrete specializes in creating driveways and curbs for the residential market. Its accounting software uses exclusive OR (XOR) operations to convert the individual bits of a plaintext message into ciphertext. The rules are as follows: In other
> Consider the employee record in Figure 15-4, which illustrates the data structure of an employee table. Given the importance of this information, it is likely that the database developer would install validation tests to ensure its accuracy. Some possibl
> The information in Figure 15-18 is for the employees of the Marcia Felix Corporation. a. Use a DBMS software package to create a database for this figure. b. What is the average pay rate for these employees? c. What is the average pay rate
> Use the Web to find current examples of data warehousing software. Why do companies create data warehouses, and what are some accounting uses of such warehouses?
> The Query Corporation employs the individuals listed in Figure 15-17. Use Access or another DBMS as required by your instructor to create a database of this information and then perform the following queries. a. List all employees in Department 5. b. Lis
> Create a Salesperson table and a Customer Order table. The salesperson table should include the salesperson number, first name, last name, commission rate, and date of last sale. The customer order table includes the order number, customer
> Bonadio Electrical Supplies distributes electrical components to the construction industry. The company began as a local supplier 15 years ago and has grown rapidly to become a major competitor in the north central United States. As the business grew and
> The quotation at the beginning of this chapter suggested that very few checks are made to check the database is not doing things it should not be doing.” What are some things that accounting database should not do? Compile a list of items, and for each o
> Give some examples of attributes you would include in a Customer table. Would you use one data field or two for the customer name? Why?
> Draw an entity–relationship diagram for the following: An accounting firm holds recruiting events for college students. At these events, recruiters are seeking students with particular skills.
> Draw an entity–relationship diagram for the following: Sales of inventory are made to customers by salespeople. After the sale, cash is received by cashiers.
> The Anderson Manufacturing Company (AMC) is located in Las Vegas, Nevada, and manufactures specialty parts for high-end sports cars. The company currently has an accounting information system, but over time, has found that it would like its system to do
> What attributes (i.e., table columns) would you be likely to include in a Cash table and in a Cash Receipts table?
> An internal auditor should have a sound understanding of basic data processing concepts such as data organization and storage in order to adequately evaluate systems and make use of retrieval software. a. Define the following terms as used in a data proce
> Do you understand Gantt charts? Use Figure 13-11 and test your understanding by answering the following questions. a. When is the activity “convert data files” scheduled to begin and end? b. When is the
> Do you understand PERT charts? Refer back to Figure 13-10 and answer the following questions: a. Which activity or activities must be completed before activity C can begin? b. Which activity or activities must be completed before activity G can begin? c.
> Identify a particular information system that is not working very well and perform a preliminary investigation of it. In your work, be sure to talk to (1) at least one external “customer” who is affected by the system, (2) one employee who uses the syste
> Are software developers cheap or expensive? That’s important because developing custom software for your accounting system depends in part on how much such labor will cost. To find out, access government statistics from the Bureau of Labor Statistic’s Occ
> Cook Consultants is currently in the process of completing the systems implementation activities for converting Samuel Company’s old system to a new one. Because of unexpected delays in performing specific implementation activities, Jerry Hazen, the proje
> Guess Right Consultants is a New Zealand business that helps clients with financial planning—especially preparing wills, creating trusts, and allocating funds among competing investment categories. It’s not an unusual business, but the company has not bee
> Jay Beck works for the AAZ Consulting Firm. His friend, Hank Henley, is the general manager and majority stockholder of the Pacific Worldwinds, a professional football team. Hank asked Jay to design an online, real time computer system for “the efficient o
> Even if you are now only a student with limited or no work experience, it is not too early to begin building a professional identity and your own company—Me, Inc. This is an identity that you’ll want to post and carefully cultivate on some of the popular
> Stevenson Apparel is a manufacturer of fashion apparel that has just opened its first large retail store for selling in-season clothes at regular prices. The company’s competitive strategy depends on a comprehensive point of-sale (POS) system supporting o
> The Chris Hall Company manufactures and distributes low-priced bottled wines to retailers. You are hired as a management consultant to help this company solve some of its systems problems. Describe the types of decision-making information that probably w
> Visit the website “How Flowcharts Help Companies Save Money, Get Accurate Audits, and Satisfy the Government” at: http://mapthink .blogspot.com/2012/10/how-flowcharts-help -companies-save.html. According to this site, how do flowcharts help save companies
> Follow the directions in Problem 12-11 to access Excel’s drawing tools, and then recreate the two program flowcharts shown in Figure 12-21. Draw each flowchart on a separate work sheet. Rename the ï&no
> The Bridget Joyce Company is an office products distributor that must decide what to do with delinquent credit-sales accounts. Mr. Bob Smith, the credit manager, divides accounts into the following categories: (1) accounts not past due, (2) accounts 30 da
> The Jeffrey Getelman Publishing Company maintains an online database of subscriber records, which it uses for preparing magazine labels, billing renewals, and so forth. New subscription orders and subscription renewals are keyed into a computer file from
> The LeVitre and Swezey Credit Union maintains separate bank accounts for each of its 20,000 customers. Three major files are the customer master file, the transaction file of deposits and withdrawal information, and a monthly statement file that shows a cust
> The order-writing department at the Winston Beauchamp Company is managed by Alan Most. The department keeps two types of computer files: (1) a customer file of authorized credit customers and (2) a product file of items currently sold by the company. Both o
> Amanda M is a regional manufacturer and wholesaler of high-quality chocolate candies. The company’s sales and collection process is as follows. Amanda M makes use of an enterprise-wide information system with electronic data interchange (EDI) capability.
> The data-entry department of the Ron Mitchell Manufacturing Company is responsible for converting all of the company’s shipping and receiving information to computer records. Because accuracy in this conversion is essential, the firm employs a strict veri
> There are many accounting blogs on the Internet. Here are some examples. Education Accounting Coach (www.accountingcoach.com/blog) The Accounting Onion (www.accountingonion.com) Sleep on CPA (http://sleeponcpa.blogspot.com/) Fraud The Forensic Accounting
> The Garcia-Lanoue Company produces industrial goods. The company receives purchase orders from its customers and ships goods accordingly. Assuming that the following conditions apply, develop a document flowchart for this company: a. The company receives
> Develop a document flowchart for the following information flow. The individual stores in the Mark Goodwin convenience chain prepare two copies of a goods requisition form (GRF) when they need to order merchandise from the central warehouse. After these fo
> Draw a document flowchart to depict each of the following situations. a. An individual from the marketing department of a wholesale company prepares five copies of a sales invoice, and each copy is sent to a different department. b. The individual invoices
> To view the flowchart shapes in Microsoft Excel, select the following options from the main menu: Insert\Shapes. There should be many of them (using Excel 2016), including many flowcharting symbols. If you allow your mouse t
> Download a copy of the Association of Certified Fraud Examiners Fraud Prevention Checkup, which is available at: www.acfe .com/uploaded Files/ACFE_ Website/Content/ documents/Fraud_Prev_Checkup_DL.pdf. On a separate piece of paper, list the seven areas an
> What company policies or procedures would you recommend to prevent each of the following activities? a. A clerk in the human relations department creates a fictitious employee in the personnel computer file. When this employee’s payroll check is received f
> The U.S. Department of Justice, Office of the U.S. Attorney press release site (www.justice .gove/usao/pressreleases) is a good source for current cybercrimes and fraud. Find a description of a cybercrime not already discussed in this chapter and prepare
> Comment on each of the following scenarios in light of chapter materials. Hint: Use the references at the end of this chapter to help you. a. A legitimate student calls the computer help desk from her cell phone because she has b. An employee at a buildi
> Assume that you started your own law practice 10 years ago, specializing in estate planning, and you currently employ five attorneys, two legal assistants, one legal secretary, and a bookkeeper/receptionist. The firm has always used a manual accounting sys
> How, assume that you work in the internal audit function at a large hospital that is considering a software package to automate the process of complying with the requirements of the American Recovery and Reinvestment Act of 2009 (commonly referred to as
> The following stated policies pertain to the-commerce website for Small Computers, Inc., a personal and handheld computer manufacturer and seller. Privacy Statement We will only use information collected on this website for legitimate business purposes.
> Describe the differences between general-use software and generalized audit software. How might you use spreadsheet software, database software, and word processing software in conducting an audit of fixed assets?
> Choose an industry described in this chapter and find out what vertical market accounting software is available for that industry. You may use resources such as the Internet, trade associations, interviews with organizations within the industry, or interv
> Save Today is a national discount retail store chain with annual revenues of more than $1 billion. It’s a typical bricks-and-mortar operation with accounting software that records sales transactions in real time and tracks inventories on a perpetual basi
> Figure 8-14 is a system flow chart for P. Miesing and Company’s purchase order preparation. Prepare a narrative to accompany the flow chart describing this purchase order preparation process. Include in you
> Novelty Gadgets is a marketer of inexpensive toys and novelties that it sells to retail stores, specialty stores, and catalog companies. As an accountant working for the company, you have been asked to design a product code for the company. In analyzing
> Listed below are several types of accounting data to be coded. For each data item, recommend a type of code (mnemonic, sequence, block, or group) and support your choice. a. Employee identification number on a computer file b. Product number for a sales ca
> To achieve effective separation of duties within a company’s IT environment, the company’s accounting and information processing subsystems should be separate from the departments that use data and perform operational activities. Discuss some of the ways
> Identify one or more control procedures (either general or application controls, or both) that would guard against each of the following errors or problems. a. A bank deposit transaction was accidentally coded with a withdrawal code. b. The key-entry ope
> The Blatz Furniture Company uses an online data input system for processing its sales invoice data, salesperson data, inventory control, and purchase order data. Representative data for each of these applications are shown in Figure 7-14. Identify speci&
> Disgruntled employees can be a significant source of problems for any company as we indicate in this problem. Andi Boyd is a very accomplished computer programmer, but she had a grudge against the company because she did not get a promotion that she thoug
> Identify one or more control procedures (either general or application controls, or both) that would guard against each of the following errors or problems. a. Leslie Thomas, a secretary at the university, indicated that she had worked 40 hours on her re
> Pucinneli Supermarkets is similar to most other grocery store chains that use the 12-digit UPC code on packages to check out customers. For a variety of reasons, it is important that the computer systems using these codes validate them for accuracy and c
> The management of Wiley Coyote Inc. decided that they needed an outside consultant to help them determine which application controls should be implemented for the company’s accounting data processing. In one of the workshops, the seminar leader, Margaret
> Susan Boyd graduated summa cum laude from State University as an accounting major and is now working for a medium-size company. Susan was very clever and quickly realized that she could set up several dummy companies that would direct the company compute
> You have been retained as a consultant to the Bentley Company, and the primary reason they think they need your expertise is to networked PCs. The company maintains fairly extensive databases regarding its customers. These databases include customer profi
> Ron Mitchell is currently working his first day as a ticket seller and cashier at the First Run Movie Theater. When a customer walks up to the ticket booth, Ron collects the required admission charge and issues the movie patron a ticket. To be admitted in
> Listed are 12 internal control procedures or requirements for the expenditure cycle (purchasing, payroll, accounts payable, and cash disbursements) of a manufacturing enterprise. For each of the following, identify the error or misstatement that would be
> The Ashland Company recently hired you to review its control procedures for the purchase, receipt, storage, and issuance of raw materials. You prepared the following comments, which describe Ashland’s procedures. • Raw materials, which consist mainly of
> Rogers, North, & Housour, LLC, is a large, regional CPA firm. There are 74 employees at their Glen Allen, SC office. The administrative assistant at this office approached Mr. Rogers, one of the partners, to express her concerns about the inventory of misce

