Question: Using Figure 8.9, Figure 8.9
Using Figure 8.9,
Figure 8.9:
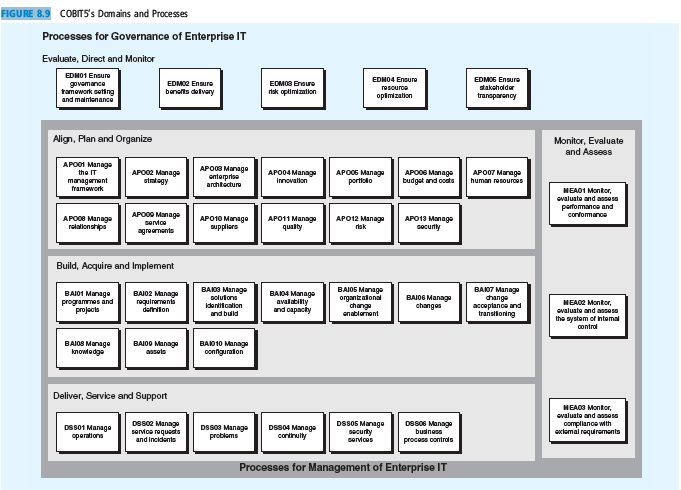
Select one COBIT process in each COBIT domain and find a specific control plan from the chapter that you believe would be categorized in the process. You will have five answers. For example: A requirements walkthrough would be a plan suitable for BAI02.
Transcribed Image Text:
FIGURE 8.9 COBITS's Damains and Processes Processes for Governance of Enterprise IT Evaluate, Direct and Monitor EDHO1 Ensure EDH04 Ensure EDMOS Engure EDMO2 Ensure EDMOS Ensure govemance tamowork seting and malntenance rosouroe takaholdar banefts delvery riak optimization opimization transparenoy Align, Plan and Organize Monitor, Evaluate and Assess APO01 Manage APO02 Manage statogy APOO Manage onterprise archtecture APO07 Manage human resouroos the IT managoment framowork APO04 Manago Innovation APO0S Manage portiolo APO0S Manage budget and oodts HEA01 Montor, ovaluate and assoss parfomance and confomance APO08 Manage relalionshipa APO00 Manage sertce agreemants APO10 Manage suppliers APO11 Manage qualty APO12 Manage risk APO13 Manage socurty Build, Acquire and Implement BAKO Manage BAI01 Manage programmes and projects BAI02 Manage requiraments BAD4 Manage avalabilty and capacly BAIOS Manage organtzalonal change enablement BAO7 Managa change accoplanoe and transtloning BAIOG Manago changes solulons Identitoation HEA02 Montor, ovaluato and asosa definiion and bulld the system of intemal contral BAIOS Manage knowlodge BAI00 Managa assels BAID10 Manage connguralon Deliver, Service and Support HEA03 Montor, ovaluata and assess DSSOS Manage security serices DSSOS Manage DS801 Manage operationa DSso2 Manage servoe requeats and incidents DSs03 Managa problems DSS04 Manage contirulty oomplianoe with oxtemal requiremants buinoss process controls Processes for Management of Enterprise IT
> What is a model? How is modeling a database or information system useful and important from a business or accounting perspective?
> Why must you have knowledge of a system’s objectives to study that system?
> What is the relationship between business intelligence (BI) and enterprise systems, especially ERP systems?
> The centralized database approach to data management is a good alternative to using enterprise systems such as ERP and CRM.” Do you agree? Discuss fully.
> What are the different logical database models (or structures)?
> What problems are solved by transforming a set of relational tables from second normal form (2NF) to third normal form (3NF)?
> What is three-tier architecture? What are some of its advantages over two-tier architecture?
> What are the differences between a logical view and a physical view of a database? Which would be more important for accountants who are involved in the design of a database that will store business event information?
> How is a DBMS different from a database?
> What is data independence? Why is it important in a comparison of application and database approaches to storing data?
> How has the technological availability and implementation of DBMSs benefited decision makers in organizations?
> What are the comparative advantages of the various data coding types discussed in Technology Summary 5.2 when applied to each of the following? Discuss fully.
> Why might you have more trouble assessing the success of a not-for-profit organization or federal government entitlement program than you would have judging the success of a business organization?
> Demonstrate your understanding of some of the coding schemes discussed in Technology Summary 5.2 by indicating which type of code is represented by each of the following. You should be prepared to explain and defend your answers.
> Why have object-oriented databases not replaced relational databases in business information system applications?
> What are the basic components of a database management system (DBMS)? Discuss the relationship between the components of DBMS and the functional model of information systems discussed in Chapter 1.
> Because there are computer-based documentation products that can draw data flow diagrams and systems flowcharts, learning to draw them manually is a waste of time.” Do you agree? Discuss fully.
> PCAOB Audit Standard No. 5 (AS5) paragraph 37 and Statement on Auditing Standard Section 319 (AU 319) paragraph 75 suggest that management, business process owners, and auditors prepare and analyze systems documentation to understand the flow of transact
> If we document a system with a system flowchart and data flow diagrams, we have over documented the system.” Discuss fully.
> Why has the Internet enabled an explosion in e-business when EDI has been available for decades?
> Discuss the benefits of SOAs to the growth of e-business.
> How does Internet EDI differ from traditional EDI in process? In result?
> Why is it important to have standards, such as X12 and EDIFACT, when conducting EDI transactions and other forms of e-business? Is there a downside to using standards?
> Examine Figure 1.1. Based on your college education to date, with which elements are you comfortable? With which are you least comfortable? Discuss your answers. FIGURE 1.1 Elements in the Study of Accounting Information Systems Technology Account
> What are some of the advantages and disadvantages of conducting business on the Internet? Be prepared to explain your answer.
> How does (or could) your university bookstore use technology to improve customer interactions with students, faculty, and staff
> Consider your favorite fast food chain restaurant. How do you think this restaurant might use OLTE to improve its business event data-processing activities? Explain.
> Consider a business where you shop. Could it operate without automated information systems? Why or why not?
> Some potential e-business customers have security concerns regarding online purchases. How do Internet security certifications attempt to address these concerns?
> One of Amazon.com’s marketing strengths is the capability to collect and analyze customer purchase data. How does this add value to the company? From the customer’s perspective, is value added?
> The business environment is increasingly demanding the use of OLRT systems for more up-to-date information. Identify one business process and the environment in which it would be used as an example of why immediate mode processing is so critical. Be prep
> Describe the primary and supporting activities involved in an organization’s value chain. Explain the importance of having an effective value chain.
> In what circumstances would a company choose a best-of-breed approach over a traditional ERP system?
> Why might a firm decide to implement only certain modules in an ERP system rather than a complete implementation?
> Examine Figure 1.1. Based on any work experience you have had, with which elements are you least comfortable? With which are you most comfortable? Discuss your answers. FIGURE 1.1 Elements in the Study of Accounting Information Systems Technology
> The following is a list of six control plans from this chapter, and these are followed by a list of five definitions or descriptions of control plans. Match the five definitions or descriptions with a control plan that best matches the definition. Becaus
> Fraud is sometimes discovered when looking at one piece of information within the context of overall data. For example, sales entered into the system after a store closes. Describe how using an Enterprise System might be preferable to a nonintegrated sys
> Provide an example of a business event. Explain how an enterprise system can provide the ability to share information and make the execution of the event efficient. Also, describe the various aspects of the business event that a company might want to cap
> Consider the inventory of a retailer. Describe how the qualities of information presented in this chapter, can help enable the efficiency and effectiveness of the organization?
> Match the items in the following two lists by matching the letter (or letters) of the information quality (qualities) that best describes the information quality violation presented in the second column. Some letters may not be used at all and some may b
> There are many opportunities for fraud within the OE/S process. One of these opportunities is the use of the system to fraudulently ship goods to an employee, posing as a customer. Describe the controls that can be implemented to reduce the likelihood th
> The following is a list of six control plans from this chapter or from Chapter 9. These are followed by a list of six statements describing either a control goal or a system deficiency. Match the five control goals or system deficiencies with a control p
> Assume that a computerized credit-checking procedure operates as follows: As orders are entered into the computer by a CSR, the computer calculates the total of the customer order and adds to this the customer’s outstanding balance from the accounts rece
> Describe a situation in which information would be shared between two of the “silos” in Figure 2.2. What data would be shared? Why would the data be shared? FIGURE 2.2 Value Chain and Value System a Organisstion
> Using the following table as a guide, describe for each function from Figure 10.1: Figure 10.1: a. A risk (an event or action that will cause the organization to fail to meet its goals/objectives) b. A control/process or use of technology that will ad
> The chapter presented a brief example of how the OE/S process might or might not support the decision-making needs of marketing managers. For each of the functional positions shown in the organization chart of Figure 10.2 (pg. 361), Figure 10.2: Spec
> Among the three functional entities (marketing, finance, and logistics) shown in Figure 10.1 (pg. 359), Figure 10.1: What goal conflicts could exist, and how might this affect the results of the OE/S process? FIGURE 101 A Haraontal Perspecive of
> Figure 9.10: Lists 10 control plans from this chapter and three control goals for the information process. Fill in the table cells, as appropriate, to indicate which control plans can accomplish which control goals. Number your entries, and describe th
> Figure 9.9 (p. 346) depicts the transmission of an electronic message incorporating public key cryptography, encryption, and digital signatures. Answer the following questions related to that figure: 1. Can anyone read the message? Why? 2. Can Sally be s
> Search the Internet or an organization to which you have access (e.g., university, your employer) to find a company policy related to employees (e.g., hiring policy) or IT (e.g. password policy). Summarize the policy and explain how the policy enhances p
> Research the Internet, newspapers, magazines, and journals to find a recent fraud case involving IT and pervasive controls failure. Develop a report (format and length to be determined by your instructor) briefly describing the case, what pervasive contr
> 1. Using a key of 2 and an algorithm of adding and subtracting from alternating letters starting with addition, encrypt the word “accounting.” 2. Using a key of 3 and an algorithm of adding and subtracting from alternating letters starting with subtracti
> The following is a list of six control plans from this chapter, followed by a list of five situations that have control implications. Match each of the five situations with the control plan that would best prevent the system failure from occurring. Becau
> Consider a business process that you have experienced at work, as a customer, or as a student. Examples might include any process in a work setting, such as payroll and purchasing, or any process with which you have interacted, such as ordering from a We
> The following is a list of six control plans from this chapter, followed by a list of five situations that have control implications. Match each of the five situations with a control plan that would best prevent the system failure from occurring. Because
> Match the concept in List 1 with the definition or description in List 2. There is only one correct or best answer for each match. Therefore, you should have three letters left over from List 1. List 1—Terms A. Pervasive control plan B. Preventive contro
> Match the concept in List 1 with the definition or description in List 2. There is only one correct or best answer for each match. Therefore, you should have three letters left over from List 1. List 1—Terms A. Input accuracy B. Input validity C. Pervasi
> Provide a comparison of the internal control frameworks of COSO’s ERM and SAS No. 78/COSO 2013 Internal Control – Integrated Framework. Discuss (in a manner prescribed by your professor) the implications to independent auditors of the differences.
> Examine the REA model for Hera Industrial Supply that appears in Figure 6.18. Figure 6.18: For each of the six entities in the model, list the attributes that a database designer should include in each table. Identify primary key attributes with (PK
> Examine the REA model for Hera Industrial Supply that appears in Figure 6.18. Figure 6.18: Determine the maximum cardinalities for each of the eight relationships indicated in the model. State any assumptions you needed to make, and be prepared to d
> Examine Figure 6.18, which contains the REA model for Hera Industrial Supply (HIS). The model is partially completed; it includes all entities and relationships, but it does not include cardinalities or descriptions of the relationships (which would appe
> Using the vendor and purchase order tables from Short Problem 6-3 and SQL commands, create a query to find out the date of each purchase order and the vendor by name each purchase order was sent to.
> Using SQL commands, create a vendor table and purchase order table, and populate them with data.
> Develop the REA data model from Short Problem 6-1 into an E-R diagram with maximum cardinalities. Assume that each inventory item can be ordered multiple times. Draw the model using Microsoft Visio (or other software).
> Describe how an enterprise system can assist an organization in optimizing its value system.
> Develop an REA data model for ordering inventory. Consider this a single event. You will need to identify the associated resource(s) and agent(s). Draw the model using Microsoft Visio (or other software).
> Using database software (e.g., Access) and the database tables implemented in SP 5-3, run a query identifying customers by name and the inventory item(s) they received by description. Obtain a printout of the query design and the results.
> Implement the E-R diagram from SP 5-1 as tables in a database software package, such as Access. Once the tables are created, link the tables together in relationships. Finally, populate the tables with several instances of each entity. To do this, it wil
> Using the E-R diagram in from SP 5-1, write a description for each of the relationships in the diagram. In your description, include the cardinalities. For example, you might describe the relationship between CUSTOMERS and SHIPMENTS as: “Shipments are ma
> Using Microsoft Visio (or an alternative software), create an E-R diagram with maximum cardinalities for the shipping of inventory to customers. Show this diagram as an REA model identifying resources, events, and agents.
> Historically, many businesses served only local customers. That model usually limited customers to a small geographic area. Identify a specific type of business, and compare/contrast the opportunities and risks for the business pre-Internet, and in today
> Identify a specific situation in which periodic processing is sufficient to support the business process, and a second situation where immediate processing is necessary to adequately support the process.
> E-business has allowed companies to reduce inventory while simultaneously offering a wide variety of items. Amazon.com is an example of such a company. Identify another organization that has expanded or improved (or could potentially expand or improve) b
> Provide an example of a business where the evolution of communication (i.e., face-to-face, phone, e-mail, etc.) has altered its business activities. What are the advantages and disadvantages associated with these changes?
> Some people believe that an automated accounting system is always better than a manual system. Describe circumstances, and provide examples, where you would recommend a manual system rather than automated solution.
> Periodically, you will read in the news about one company in the ERP industry acquiring another company in that industry. Discuss the pros and cons of consolidation of the ERP software industry.
> Enterprise systems may provide better information than nonintegrated systems for management decisions. Provide specific examples that support (or refute) this claim.
> Consider the business event–processing activity, entering a customer’s order. Identify the key business event data (who, what, where, and when) you would want to capture. (For an example of the event you may refer to F
> Find the most current listing of the AICPA’s or CPA Canada’s Top Technology Initiatives Survey. Research and write a paper on the accounting and business implications for the number one item on the list. Include any external pressures that may impact the
> Identify the skills required to be a forensic accountant. How does the knowledge of technology and AIS help enable or augment those skills?
> Find the most current listing of the AICPA’s or CPA Canada’s Top Technology Initiatives Survey. Compare the listing to prior years’ listings. Identify and discuss trends among the years. Your professor will tell you how long your paper should be.
> About three decades ago, in his first address as Chairman of the Board of the American Institute of Certified Public Accountants (AICPA), Robert K. Elliott said: Knowledge leveraging will shape a wide range of CPA services. CPAs will be able to identify
> The following is a brief description of the financial statement assertions from PCAOB Auditing Standards Section AU 326, Evidential Matter: A. Existence or occurrence: Assets or liabilities of the entity exist at a given date (existence) or recorded tran
> The following is a list of 12 control plans from this chapter, followed by a list of 10 examples of System Failures or problem situations that have control implications: Match the 10 system failures with a control plan that would best prevent the system
> The following narrative describes the processing of customer mail orders at Eye-Dee-A-Pet, Inc.: Eye-Dee-A-Pet, Inc. is a small manufacturing operation engaged in the selling of digital identification chips that can be implanted into household pets, such
> Research the Internet, newspapers, magazines, and journals to find recent incidences of denial-of-service attacks on one or more Web sites. Develop a report (format and length to be determined by your instructor) providing a general overview of the incid
> The Tigris Company is considering taking customers’ orders on its Web site. a. What information would Tigris collect from the customer during this process? b. What information would need to come from Tigris’ Web and back-end systems to complete the order
> Research the Internet, newspapers, magazines, and journals to find recent incidences of outages of one or more Web sites. Develop a report (format and length to be determined by your instructor) providing a general overview of the incident(s), including
> Examine the last column in Table 8.2 (p. 280) for the following personnel only: access control officer, chief information officer (CIO), structural security/disaster recovery manager, testing/quality assurance, and database administrator. For each of the
> AS5 outlines the processes for “An Audit of Internal Control over Financial Reporting That Is Integrated with an Audit of Financial Statements.” Paragraph 24 of this document lists eight entity-level controls. Entity-level controls are comparable to the
> Personnel at C&P Company must perform the following functions: 1. Receive checks and remittance advice from customers. 2. Approve vendor invoices for payment and prepare checks. 3. Approve credit memoranda for customer sales returns. 4. Record collection
> Assume that accounts payable are processed on a computer and that the options in the accounts payable system module are as follows: 1. Maintain vendor master data (i.e., add, change, or delete vendors in the vendor master data). 2. Record vendor invoices
> The following is a list of 13 control plans from this chapter, followed by a list of 10 situations that have control implications. Match the 10 situations with the control plan that would best prevent the system failure from occurring. Because there are
> Listed here are 20 control plans discussed in the chapter. On the blank line to the left of each control plan, insert a P (preventive), D (detective), or C (corrective) to classify that control most accurately. If you think that more than one code could
> The following is a list of 10 common security problems. For each problem, describe why it is a problem and choose a control plan from this chapter that would prevent or detect the problem from occurring. a. Criminals posing as small business owners obtai
> Figure 7.8: depicts the adaptation of a sample control matrix from a PricewaterhouseCoopers guide for Section 404 of the Sarbanes-Oxley Act of 2004.28 We have added some data from the Suprina Company example to the first row of the matrix. Compare the
> The CFO of PKD Corporation is very uncomfortable with its current risk exposure related to the possibility of business disruptions. Specifically, PKD is heavily involved in E-business, and its internal information systems are tightly interlinked with its
> After the core of an ERP system has been implemented, any of the modules may then be implemented separately. What is the implication of being able to implement an ERP system on a piece-by-piece basis?
> In the following first list are 10 examples of the items described in the second list. Match the two lists by placing the capital letter from the first list on the blank line preceding the description to which it best relates. You should have two letters
> Following is a list of eight generic control goals from the chapter, followed by eight descriptions of either process failures (i.e., control goals not met) or instances of successful control plans (i.e., plans that helped to achieve control goals). List

