Question: A supplement to the X.25 packet-
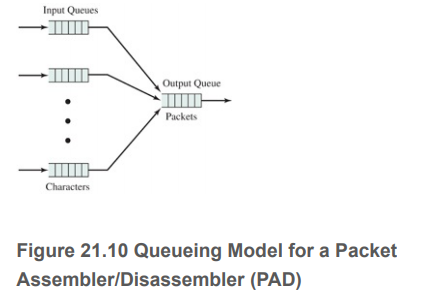
A supplement to the X.25 packet-switching standard is a set of standards for a packet assembler-disassembler (PAD), defined in standards X.3, X.28, and X.29. A PAD is used to connect asynchronous terminals to a packet-switching network. Each terminal attached to a PAD sends characters one at a time. These are buffered in the PAD then assembled into an X.25 packet that is transmitted to the packet-switching network. The buffer length is equal to the maximum data field size for an X.25 packet. A packet is formed from assembled characters and transmitted whenever the buffer is full, a special control character such as a carriage return is received, or when a timeout occurs. For this problem, we ignore the last two conditions. Figure 21.10 illustrates the queueing model for the PAD. The first queue models the delay for characters waiting to be put into a packet; this queue is completely emptied when it is filled. The second queue models the delay waiting to transmit packets. Use the following notation:
λ=Poisson input rate of characters from each termina.l
C=Rate of transmission on the output channel in characters per second.
M=Number of data characters in a packet.
H=Number of overhead characters in a packet.
K=Number of terminals.
a. Determine the average waiting time for a character in the input queue.
b. Determine the average waiting time for a packet in the output queue.
c. Determine the average time spent by a character from when it leaves the terminal to when it leaves the PAD. Plot the result as a function of normalized load.
Transcribed Image Text:
Input Queues Output Queue Packets Characters Figure 21.10 Queueing Model for a Packet Assembler/Disassembler (PAD)
> Why does the eCos bitmap scheduler not support time slicing?
> In Table Q.1, what limitations should be placed in the use of/. Table Q.1: cyg_drv_mutex_destroy? Table Q.1 Device Driver Interface to the eCos Kernel: Concurrency cyg_drv_spinlock_init Initialize a spinlock in a locked or unlocked state. cyg_drv_sp
> Virtual machines are presented with storage in manners similar to physical machines via TCP/IP, Fibre-Channel, or iSCSI connections. There are features in virtualization that optimize memory and processor usage, and advanced features that can provide mor
> Providing additional bandwidth for virtualization servers initially involved additional network interface cards (NICs) for more network connections. With the advent of increasingly greater network backbone bandwidths (10Gbit/s, 40Gbit/s, and 100Gbit/s)
> Suppose there are two types of philosophers. One type always picks up his left fork first (a “lefty”), and the other type always picks up his right fork first (a “righty”). The behav
> How is the process address space handled during process migration?
> When virtualization first appeared in the x86 marketplace, many server vendors were skeptical of the technology and were concerned that consolidation would impact the sales of servers. Instead, server vendors found that they were selling larger, costlier
> Type 1 hypervisors operate directly on physical hardware without any intervening operating system. Type 2 hypervisors run as an application installed on an existing operating system. Type 1 hypervisors perform much better than Type 2 hypervisors since th
> Which type of process is generally favored by a multilevel feedback queuing scheduler—a processor-bound process, or an I/O-bound process? Briefly explain why.
> Consider the organization of a UNIX file as represented by the inode (see Figure 12.15). Assume there are 12 direct block pointers, and a singly, doubly, and triply indirect pointer in each inode. Further, assume the system block size and the disk sector
> In UNIX System V, the length of a block is 1 Kbyte, and each block can hold a total of 256 block addresses. Using the inode scheme, what is the maximum size of a file?
> Consider a hierarchical file system in which free disk space is kept in a free space list. a. Suppose the pointer to free space is lost. Can the system reconstruct the free space list? b. Suggest a scheme to ensure that the pointer is never lost as a res
> The discussion of eCos spinlocks included an example showing why spinlocks should not be used on a uni-processor system if two threads of different priorities can compete for the same spinlock. Explain why the problem still exists even if only threads of
> Techniques like memory over commit and page sharing permit virtual machines to be allocated more resources than are physically in a single virtualization host. Does this allow the aggregate of the virtual machines to perform more real work than a physica
> In Table Q.1, what should be the limitations on the use of / Explain? Table Q.1: cyg_drv_spinlock_destroy? Table Q.1 Device Driver Interface to the eCos Kernel: Concurrency cyg_drv_spinlock_init Initialize a spinlock in a locked or unlocked state. c
> Also in Table Q.1, it is recommended that / should be used sparingly, and in situations where deadlocks/livelocks cannot occur. Explain why. Table Q.1: cyg_drv_spinlock_spin Table Q.1 Device Driver Interface to the eCos Kernel: Concurrency cyg_drv_
> What characteristics distinguish the various elements of a memory hierarchy?
> With reference to the device driver interface to the eCos kernel (see Table Q.1), it is recommended that device drivers should use the / variants to claim and release spinlocks rather than the non- / variants. Explain why Table Q.1: intsave ()
> a. The TinyOS Resource interface does not allow a component that already has a request in the queue for a resource to make a second request. Suggest a reason. b. However, the TinyOS Resource interface allows a component holding the resource lock to re-re
> TinyOS’s scheduler serves tasks in FIFO order. Many other schedulers for TinyOS have been proposed, but none have caught on. What characteristics of the sensornet domain might cause a lack of need for more complex scheduling?
> Suggest pros and cons for fat client and thin client strategies.
> What are fat clients and thin clients, and what are the differences in philosophy of the two approaches?
> Discuss the rationale for locating applications on the client, the server, or split between client and server.
> What is the role of a communications architecture such as TCP/IP in a client/server environment?
> What distinguishes client/server computing from any other form of distributed data processing?
> What is client/server computing?
> What conditions are generally associated with the readers/writers problem?
> A fraction P of the traffic from a single exponential server is fed back into the input as shown in Figure 21.11. In the figure, Λ denotes the system throughput, which is the output rate from the server. Figure 21.11: a. Determine the syste
> What is the difference between demand cleaning and precleaning?
> List and briefly define three file allocation methods.
> What is RIOT?
> What requirements should an IoT OS satisfy?
> List and briefly define the principal components of an IoT-enabled thing.
> Define the Internet of Things.
> What is the purpose of the Sockets interface?
> What is TCP/IP?
> What is a protocol architecture?
> What is a protocol?
> How are multiple interrupts dealt with?
> What tasks are performed by the transport layer?
> What is the major function of the network access layer?
> What is OpenStack?
> What is the relationship between a cloud OS and IaaS?
> List and briefly define the key components of a cloud operating system.
> What is the cloud computing reference architecture?
> List and briefly define three cloud service models.
> Define cloud computing.
> What is the default scheduling discipline for TinyOS?
> What software comprises the TinyOS operating system?
> List and briefly describe some of the defenses against buffer overflows that can be implemented when running existing, vulnerable programs
> List and briefly describe some of the defenses against buffer overflows that can be used when compiling new programs.
> What are the two broad categories of defenses against buffer overflows?
> What types of programming languages are vulnerable to buffer overflows?
> Briefly describe the difference between DAC and RBAC.
> In general terms, what are four means of authenticating a user’s identity?
> List and briefly define three classes of intruders.
> What are typical access rights that may be granted or denied to a particular user for a particular file?
> What is a TinyOS component?
> What are the design goals for TinyOS?
> What is an interrupt?
> What is the target application for Tiny OS?
> Explain the relative advantages and disadvantages of an embedded OS based on an existing commercial OS compared to a purpose-built embedded OS.
> Give a brief description of Java VM.
> Explain the concept of ballooning.
> Briefly describe container virtualization.
> Briefly describe Type 1 and Type 2 virtualization.
> What are some of the key characteristics of an embedded OS?
> What is an embedded OS?
> What are some typical requirements or constraints on embedded systems?
> What is an embedded system?
> What is the difference between a mode switch and a process switch?
> List and briefly define three blocking methods.
> What are typical access rights that may be granted or denied to a particular user for a particular file?
> What is the relationship between a pathname and a working directory?
> What are typical operations that may be performed on a directory?
> Why is the average search time to find a record in a file less for an indexed sequential file than for a sequential file?
> List and briefly define five file organizations.
> What criteria are important in choosing a file organization?
> What is a file management system?
> What is the difference between a file and a database?
> What is the difference between a field and a record?
> List and briefly define four different clustering methods.
> Briefly define feedback scheduling.
> Briefly define highest-response-ratio-next scheduling.
> Briefly define shortest-remaining-time scheduling.
> What is the typical disk sector size?
> Briefly define the seven RAID levels.
> Briefly define the disk scheduling policies illustrated in Figure 11.7. Figure 11.7: 100 125 150 175 199 Time (a) FIFO 25 50 100 125 150 175 199 Time (h) SSTF 50 75 100 125 150 175 199 Time (c) SCAN 50 100 125 150 175 199 Time (d) C-SCAN Figure 11.7
> What delay elements are involved in a disk read or write?
> Why would you expect improved performance using a double buffer rather than a single buffer for I/O?
> What is the difference between block-oriented devices and stream-oriented devices? Give a few examples of each.
> What is the difference between logical I/O and device I/O?
> List some benefits and disadvantages of synchronous and asynchronous RPCs.
> List and briefly define three techniques for performing I/O.
> What items of information about a task might be useful in real-time scheduling?
> List and briefly define four classes of real-time scheduling algorithms.
> List and briefly define five general areas of requirements for a real-time operating system.
> What is the difference between periodic and aperiodic real-time tasks?
> What is the difference between hard and soft real-time tasks?
> List and briefly define three versions of load sharing.

