Question: In Table Q.1, what should be
In Table Q.1, what should be the limitations on the use of / Explain?
Table Q.1:

Transcribed Image Text:
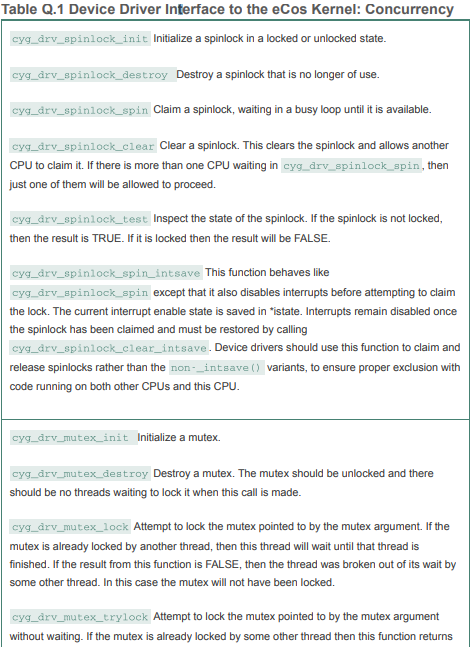
cyg_drv_spinlock_destroy? Table Q.1 Device Driver Interface to the eCos Kernel: Concurrency cyg_drv_spinlock_init Initialize a spinlock in a locked or unlocked state. cyg_drv_spinlock_destroy Destroy a spinlock that is no longer of use. cyg_drv_spinlock_spin Claim a spinlock, waiting in a busy loop until it is available. cyg_drv_spinlock_clear Clear a spinlock. This clears the spinlock and allows another CPU to claim it. If there is more than one CPU waiting in cyg_drv_spinlock_spin, then just one of them will be allowed to proceed. cyg_drv_spinlock_test Inspect the state of the spinlock. If the spinlock is not locked, then the result is TRUE. If it is locked then the result will be FALSE. cyg_drv_spinlock_spin_intsave This function behaves like cyg_årv_spinlock spin except that it also disables interrupts before attempting to claim the lock. The current interrupt enable state is saved in "istate. Interrupts remain disabled once the spinlock has been claimed and must be restored by calling cyg_drv_spinlock_clear_intsave. Device drivers should use this function to claim and release spinlocks rather than the non-_intsave () variants, to ensure proper exclusion with code running on both other CPUS and this CPU. cyg_drv_mutex_init Initialize a mutex. cyg_drv_mutex_destroy Destroy a mutex. The mutex should be unlocked and there should be no threads waiting to lock it when this call is made. cyg_årv_mutex_lock Attempt to lock the mutex pointed to by the mutex argument. If the mutex is already locked by another thread, then this thread will wait until that thread is finished. If the result from this function is FALSE, then the thread was broken out of its wait by some other thread. In this case the mutex will not have been locked. cyg_årv_mutex_trylock Attempt to lock the mutex pointed to by the mutex argument without waiting. If the mutex is already locked by some other thread then this function returns
> For Figure 19.9, it is claimed that all four processes assign an ordering of to the two messages, even though q arrives before a at Work through the algorithm to demonstrate the truth of the claim Figure 19.9: PI P4 (a,1,1) I (q.1,4) Time (local clo
> In priority-based process scheduling, the scheduler only gives control to a particular process if no other process of higher priority is currently in the Ready state. Assume no other information is used in making the process scheduling decision. Also ass
> Some have argued that Unix/Linux systems reuse a small number of security features in many contexts across the system; while Windows systems provide a much larger number of more specifically targeted security features used in the appropriate contexts. Th
> What are the advantages and disadvantages of using a file integrity checking tool (e.g., tripwire). This is a program which notifies the administrator of any changes to files on a regular basis? Consider issues such as which files you really only want to
> TFTP’s time-out-and-retransmission scheme implies that all data packets will eventually be received by the destination host. Will these data also be received uncorrupted? Why or why not?
> We have seen that in order to deal with lost packets, TFTP implements a time-out-and-retransmit scheme, by setting a retransmission timer when it transmits a packet to the remote host. Most TFTP implementations set this timer to a fixed value of about fi
> What is the difference between a multiprocessor and a multicore system?
> TFTP, like most protocols, will never send an error packet in response to an error packet it receives. Why?
> The flushing policy is described in the subsection on process migration strategies in Section 19.1. a. From the perspective of the source, which other strategy does flushing resemble? b. From the perspective of the target, which other strategy does flush
> A user on a UNIX host wants to transfer a 4,000-byte text file to a Microsoft Windows host. In order to do this, he transfers the file by means of TFTP, using the netascii transfer mode. Even though the transfer was reported as being performed successful
> What is the limiting factor in the time required to transfer a file using TFTP?
> The previous version of the TFTP specification, RFC 783, included the following statement: All packets other than those used for termination are acknowledged individually unless a timeout occurs. The new specification revises this to say All packets othe
> Why does the TCP header have a header length field while the UDP header does not?
> The following FORTRAN program is to be executed on a computer, and a parallel version is to be executed on a 32- b computer cluster: L1: DO 10 I=1,1024 L2: SUM(I)=0 L3: DO 20 J=1, I L4: 20 SUM(I)=SUM(I)+I L5: 10 CONTINUE Suppose lines 2 and 4 each take t
> An application program is executed on a nine-computer cluster. A benchmark program takes time T on this cluster. Further, 25% of T is time in which the application is running simultaneously on all nine computers. The remaining time, the application has t
> Let be the percentage of program code that can be executed simultaneously by n computers in a cluster, each computer using a different set of parameters or initial conditions. α Assume the remaining code must be executed sequentially by a single processo
> A TCP segment consisting of 1,500 bits of data and 160 bits of header is sent to the IP layer, which appends another 160 bits of header. This is then transmitted through two networks, each of which uses a 24-bit packet header. The destination network has
> Figure 6.18 shows another solution to the dining philosophers problem using monitors. Compare to Figure 6.14 and report your conclusions. Figure 6.18: Figure 6.14: monitor dining_controller; enum states (thinking, hungry, eating) state [5]; cond ne
> List the major disadvantages of the layered approach to protocols.
> For this problem, first consider the case where you wish to order pizza for a party of guests. The layer models in Figure 17.8 can be used to describe the ordering and delivery of a pizza. The guest effectively places the order with the cook. The host co
> Consider user accounts on a system with a Web server configured to provide access to user Web areas. In general, this scheme uses a standard directory name, such as , in a user’s home directory. This acts as the user’s Web area if it exists. However, to
> In the traditional UNIX file access model, UNIX systems provide a default setting for newly created files and directories, which the owner may later change. The default is typically full access for the owner combined with one of the following: no access
> UNIX treats file directories in the same fashion as files; that is, both are defined by the same type of data structure, called an inode. As with files, directories include a 9-bit protection string. If care is not taken, this can create access control p
> User “ahmed” owns a directory, “stuff,” containing a text file called “ourstuff.txt” that he shares with users belonging to the group “staff.” Those users may read and change this file, but not delete it. They may not add other files to the directory. Ot
> Set user (SetUID) and set group (SetGID) programs and scripts are a powerful mechanism provided by Unix to support “controlled invocation” to manage access to sensitive resources. However, precisely because of this, it is a potential security hole, and b
> For the DAC model discussed in Section 15.3, an alternative representation of the protection state is a directed graph. Each subject and each object in the protection state is represented by a node (a single node is used for an entity that is both subjec
> Rewrite the function shown in Figure 15.2a so it is no longer vulnerable to a stack buffer overflow. Figure 15.2a: (a) Basic buffer overflow C code $ cc -g -o bufferl buffer1.c $ . /buffer1 START bufferl: str1 (START), str2 (START), valid (1) $ ./bu
> In the context of an IDS, we define a false positive to be an alarm generated by an IDS in which the IDS alerts to a condition that is actually benign. A false negative occurs when an IDS fails to generate an alarm when an alert-worthy condition is in ef
> What is cache memory?
> Consider an automated audit log analysis tool (e.g., swatch). Can you propose some rules which could be used to distinguish “suspicious activities” from normal user behavior on a system for some organization?
> Why is logging important? What are its limitations as a security control? What are pros and cons of remote logging?
> Assume a system with N job positions. For job position i, the number of individual users in that position is and the number of permissions required for the job position is a. For a traditional DAC scheme, how many relationships between users and permissi
> State some threats that result from a process running with administrator or root privileges on a system.
> Figure 13.12 is a listing of code intended for use on the eCos kernel. Figure 13.12: a. Explain the operation of the code. Assume thread B begins execution first, and thread A begins to execute after some event occurs. b. What would happen if the mutex
> The implementation of mutexes within the eCos kernel does not support recursive locks. If a thread has locked a mutex then attempts to lock the mutex again, typically as a result of some recursive call in a complicated call graph, then either an assertio
> Why does the eCos bitmap scheduler not support time slicing?
> In Table Q.1, what limitations should be placed in the use of/. Table Q.1: cyg_drv_mutex_destroy? Table Q.1 Device Driver Interface to the eCos Kernel: Concurrency cyg_drv_spinlock_init Initialize a spinlock in a locked or unlocked state. cyg_drv_sp
> Virtual machines are presented with storage in manners similar to physical machines via TCP/IP, Fibre-Channel, or iSCSI connections. There are features in virtualization that optimize memory and processor usage, and advanced features that can provide mor
> Providing additional bandwidth for virtualization servers initially involved additional network interface cards (NICs) for more network connections. With the advent of increasingly greater network backbone bandwidths (10Gbit/s, 40Gbit/s, and 100Gbit/s)
> Suppose there are two types of philosophers. One type always picks up his left fork first (a “lefty”), and the other type always picks up his right fork first (a “righty”). The behav
> How is the process address space handled during process migration?
> When virtualization first appeared in the x86 marketplace, many server vendors were skeptical of the technology and were concerned that consolidation would impact the sales of servers. Instead, server vendors found that they were selling larger, costlier
> Type 1 hypervisors operate directly on physical hardware without any intervening operating system. Type 2 hypervisors run as an application installed on an existing operating system. Type 1 hypervisors perform much better than Type 2 hypervisors since th
> Which type of process is generally favored by a multilevel feedback queuing scheduler—a processor-bound process, or an I/O-bound process? Briefly explain why.
> Consider the organization of a UNIX file as represented by the inode (see Figure 12.15). Assume there are 12 direct block pointers, and a singly, doubly, and triply indirect pointer in each inode. Further, assume the system block size and the disk sector
> In UNIX System V, the length of a block is 1 Kbyte, and each block can hold a total of 256 block addresses. Using the inode scheme, what is the maximum size of a file?
> Consider a hierarchical file system in which free disk space is kept in a free space list. a. Suppose the pointer to free space is lost. Can the system reconstruct the free space list? b. Suggest a scheme to ensure that the pointer is never lost as a res
> The discussion of eCos spinlocks included an example showing why spinlocks should not be used on a uni-processor system if two threads of different priorities can compete for the same spinlock. Explain why the problem still exists even if only threads of
> Techniques like memory over commit and page sharing permit virtual machines to be allocated more resources than are physically in a single virtualization host. Does this allow the aggregate of the virtual machines to perform more real work than a physica
> Also in Table Q.1, it is recommended that / should be used sparingly, and in situations where deadlocks/livelocks cannot occur. Explain why. Table Q.1: cyg_drv_spinlock_spin Table Q.1 Device Driver Interface to the eCos Kernel: Concurrency cyg_drv_
> What characteristics distinguish the various elements of a memory hierarchy?
> With reference to the device driver interface to the eCos kernel (see Table Q.1), it is recommended that device drivers should use the / variants to claim and release spinlocks rather than the non- / variants. Explain why Table Q.1: intsave ()
> a. The TinyOS Resource interface does not allow a component that already has a request in the queue for a resource to make a second request. Suggest a reason. b. However, the TinyOS Resource interface allows a component holding the resource lock to re-re
> TinyOS’s scheduler serves tasks in FIFO order. Many other schedulers for TinyOS have been proposed, but none have caught on. What characteristics of the sensornet domain might cause a lack of need for more complex scheduling?
> Suggest pros and cons for fat client and thin client strategies.
> What are fat clients and thin clients, and what are the differences in philosophy of the two approaches?
> Discuss the rationale for locating applications on the client, the server, or split between client and server.
> What is the role of a communications architecture such as TCP/IP in a client/server environment?
> What distinguishes client/server computing from any other form of distributed data processing?
> What is client/server computing?
> What conditions are generally associated with the readers/writers problem?
> A fraction P of the traffic from a single exponential server is fed back into the input as shown in Figure 21.11. In the figure, Λ denotes the system throughput, which is the output rate from the server. Figure 21.11: a. Determine the syste
> What is the difference between demand cleaning and precleaning?
> List and briefly define three file allocation methods.
> What is RIOT?
> What requirements should an IoT OS satisfy?
> List and briefly define the principal components of an IoT-enabled thing.
> Define the Internet of Things.
> What is the purpose of the Sockets interface?
> What is TCP/IP?
> What is a protocol architecture?
> What is a protocol?
> How are multiple interrupts dealt with?
> What tasks are performed by the transport layer?
> What is the major function of the network access layer?
> What is OpenStack?
> What is the relationship between a cloud OS and IaaS?
> List and briefly define the key components of a cloud operating system.
> What is the cloud computing reference architecture?
> List and briefly define three cloud service models.
> Define cloud computing.
> What is the default scheduling discipline for TinyOS?
> What software comprises the TinyOS operating system?
> A supplement to the X.25 packet-switching standard is a set of standards for a packet assembler-disassembler (PAD), defined in standards X.3, X.28, and X.29. A PAD is used to connect asynchronous terminals to a packet-switching network. Each terminal att
> List and briefly describe some of the defenses against buffer overflows that can be implemented when running existing, vulnerable programs
> List and briefly describe some of the defenses against buffer overflows that can be used when compiling new programs.
> What are the two broad categories of defenses against buffer overflows?
> What types of programming languages are vulnerable to buffer overflows?
> Briefly describe the difference between DAC and RBAC.
> In general terms, what are four means of authenticating a user’s identity?
> List and briefly define three classes of intruders.
> What are typical access rights that may be granted or denied to a particular user for a particular file?
> What is a TinyOS component?
> What are the design goals for TinyOS?
> What is an interrupt?
> What is the target application for Tiny OS?
> Explain the relative advantages and disadvantages of an embedded OS based on an existing commercial OS compared to a purpose-built embedded OS.
> Give a brief description of Java VM.
> Explain the concept of ballooning.
> Briefly describe container virtualization.

