Question: Did you know: ■ Once every 3 minutes,
Did you know:
â– Once every 3 minutes, the average company comes into contact with viruses and malware.
â– One in every 291 email messages contains a virus.
â– Three things hackers want most are customer data, intellectual property, and bank account
information.
â– The top five file names used in phishing scams are Details.zip, UPS_document.zip, DCIM.zip,
Report.zip, and Scan.zip.
â– The average annual cost of a cyberattack on a small or medium-sized business is $188,242.
Cyberthieves are always looking for new ways to gain access to your business data, business
networks, and business applications. The best way to protect your business from cybertheft is to build a strong defense and be able to identify vulnerabilities and weak spots. According to John Brandon of Inc. magazine, the top five ways hackers will try to gain access to your businesses are highlighted in Figure Unit 1. (Please note that there are far more than five ways; these are just the five most common.)
Required:
1. Explain why data, information, business intelligence, and knowledge are important to successfully running a business. Be sure to list examples of for each.
2. Why would hackers want to steal organizational information?
3. What problems can occur for a business that experiences a data theft from a CRM system? Would the problems be the same is the data theft occurred from an SCM system? Why or why not?
4. Define information ethics and information security and explain whether they are important to help prevent hackers from gaining access to an organization.
5. What type of metrics would an organization gather to help identify illegal system access?
Figure 1:
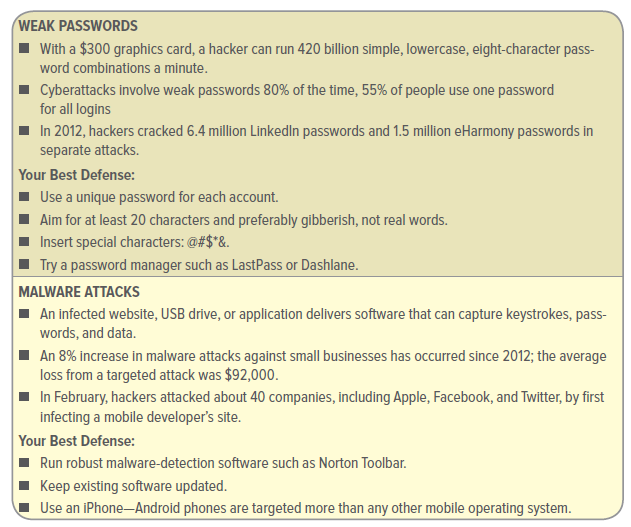

Transcribed Image Text:
WEAK PASSWORDS With a $300 graphics card, a hacker can run 420 billion simple, lowercase, eight-character pass- word combinations a minute. Cyberattacks involve weak passwords 80% of the time, 55% of people use one password for all logins In 2012, hackers cracked 6.4 million LinkedIn passwords and 1.5 million eHarmony passwords in separate attacks. Your Best Defense: Use a unique password for each account. Aim for at least 20 characters and preferably gibberish, not real words. Insert special characters: @#$*&. Try a password manager such as LastPass or Dashlane. MALWARE ATTACKS An infected website, USB drive, or application delivers software that can capture keystrokes, pass- words, and data. An 8% increase in malware attacks against small businesses has occurred since 2012; the average loss from a targeted attack was $92,000. In February, hackers attacked about 40 companies, including Apple, Facebook, and Twitter, by first infecting a mobile developer's site. Your Best Defense: ■ Run robust malware-detection software such as Norton Toolbar. Keep existing software updated. Use an iPhone-Android phones are targeted more than any other mobile operating system. PHISHING EMAILS ■ Bogus but official-looking emails prompt you to enter your password or click links to infected websites. ■ A 125% rise in social-media phishing attacks has occurred since 2012. Phishers stole $1 billion from small businesses in 2012. ■Many small businesses were targeted in 2012 with phishing emails designed to look like Better Business Bureau warnings. Your Best Defense: ■ Keep existing software, operating systems, and browsers updated with the latest patches. ■ Don't automatically click links in emails to external sites-retype the URL in your browser. SOCIAL ENGINEERING ■ Think 21st-century con artist tactics, e.g., hackers pretend to be you to reset your passwords. ■ Twenty-nine percent of all security breaches involve some form of social engineering. Average loss is $25,000 to $100,000 per incident. ■ In 2009, social engineers posed as Coca-Cola's CEO, persuading an exec to open an email with software that infiltrated the network. Your Best Defense: ■ Rethink what you reveal on social media-it's all fodder for social engineers. ■ Develop policies for handling sensitive requests such as password resets over the phone. Have a security audit done. RANSOMWARE ■ Hackers hold your website hostage, often posting embarrassing content such as porn, until you pay a ransom. ■ Five million dollars is extorted each year. The real cost is the data loss-paying the ransom doesn't mean you get your files back. ■ Hackers locked the network at an Alabama ABC TV station, demanding a ransom to remove a red screen on every computer. Your Best Defense: ■As with malware, do not click suspicious links or unknown websites. ■ Regularly back up your data. Use software that specifically checks for new exploits.¹
> Using drones to drop off packages could be great for buyers, who might want to get certain items as fast as humanly possible. Back in 2013, when Amazon revealed plans to begin delivering packages via flying drones through Prime Air, some seemed skeptical
> What are the four common characteristics of big data?
> What is big data?
> What is a click-and-mortar? Provide an example.
> What is a brick-and-mortar? Provide an example.
> What is a pure-play? Provide an example.
> Compare disruptive and sustaining technologies, and explain how the Internet and WWW caused business disruption.
> What is the difference between a B2B and a B2C?
> What are the benefits and challenges associated with ebusiness?
> How did ebusiness change traditional business models?
> What is an ebusiness model?
> What is the difference between search engine ranking and search engine optimization?
> Why is search engine ranking important to a company?
> What are the four data-mining techniques for predictions and why are they important to a business?
> What is data-driven decision management?
> What are the four data-mining techniques? Provide examples of how you would use each one in business.
> Identify the advantages of using business intelligence to support managerial decision making.
> What are the six steps in the data-mining process and why is each important?
> What is virtualization and how has it helped drive the big data era?
> What is distributed computing and how has it helped drive the big data era?
> Slack’s business model is simple: Be Less Busy. It’s hard to imagine any busy professional not coveting those simple words. Slack’s promise is to make business professionals more productive by eliminating meetings and emails. Can you imagine a life witho
> Bitcoin is a new currency that was created in 2009 by an unknown person using the alias Satoshi Nakamoto. Bitcoin isn’t just a currency, like dollars or euros or yen. It’s a way of making payments, like PayPal or the Visa credit card network. Bitcoins ca
> Identify the four common characteristics of big data.
> Identify the four challenges associated with ebusiness.
> Describe the six ebusiness tools for connecting and communicating.
> Compare the four categories of ebusiness models.
> Explain the importance of data analytics and data visualization.
> Describe the roles and purposes of data warehouses and data marts in an organization.
> Explain data mining and identify the three elements of data mining.
> Data Visualization: Stories for the Information Age At the intersection of art and algorithm, data visualization schematically abstracts information to bring about a deeper understanding of the data, wrapping it in an element of awe. While the practice
> The word gig comes from the music world; a gig is a paid appearance of limited duration. A gig economy is an environment in which temporary employment is common and organizations contract with independent workers for short-term engagements. Today’s workf
> eBay is the world’s largest online marketplace, with 97 million global users selling anything to anyone at a yearly total of $62 billion—more than $2,000 every second. Of course with this many sales, eBay is collecting the equivalent of the Library of Co
> Micheal Porter is a university professor at Harvard Business School, where he leads the Institute on Strategy and Competitiveness, studying competitiveness for companies and nations—and as a solution to social problems. He is the founder of numerous nonp
> Where are the supplier’s suppliers in a typical supply chain?
> Where are the customer’s customers in a typical supply chain?
> What is the bullwhip effect and how can it impact a supply chain and a firm’s profitability?
> What are the five primary activities in a supply chain?
> What are the three different ERP implementation choices?
> Describe Web 1.0 along with ebusiness and its associated advantages.
> How does a company measure the success of an ERP system?
> At the heart of an ERP system is a database that is capturing all of the operational system data.
> The four most common extended ERP components business intelligence, customer relationship management, supply chain management, and ebusiness.
> What are the components in a core ERP system?
> What is the difference between core and extended ERP?
> What is an enterprise resource planning system?
> What is RFID’s primary purpose in the supply chain?
> What is materials management and how does it impact the supply chain?
> What is logistics and how does it impact the supply chain?
> What is procurement and how does it impact the supply chain?
> Have you ever seen the movie Terminator in which machines take over the world? Do you think that scenario could ever come true? Researching the Internet of Things makes you wonder if robots can gain self-consciousness, making the possibility of them taki
> Describe supply chain management along with its impact on business.
> Identify the core and extended areas of enterprise resource planning.
> Describe the role information plays in enterprise resource planning systems.
> Discuss the current technologies organizations are integrating in enterprise resource planning systems.
> Identify the three components of supply chain management along with the technologies reinventing the supply chain.
> Have you ever lost a beloved pet? No worries, just draw a picture of your pet and print a plastic replica from your 3D desktop printer so your cat or dog can sit on your desk forever. Can you imagine printing your drawing in 3D? Well, there is no need to
> We are currently in the middle of the connected car revolution, a vehicle equipped with smart sensors, Internet access, and a number of information systems that make driving easy, intelligent, and safe. Connected cars share information with individuals i
> The world of ERP may seem boring to those caught up in the hysteria over Twitter and iPhone applications, but there’s plenty of drama to be found: Troubled multimillion-dollar software deals that produce spectacular failures and huge spending nightmares;
> In his book The World Is Flat, Thomas Friedman describes the unplanned cascade of technological and social shifts that effectively leveled the economic world and “accidentally made Beijing, Bangalore, and Bethesda next-door neighbors.&a
> Over 20 years ago a few professors at MIT began describing the Internet of Things (IoT), which is a world where interconnected Internet-enabled devices or “things” have the ability to collect and share data without human intervention. Another term for th
> What is the relationship between adware and spyware?
> What are the costs associated with downtime?
> What are the reasons a company experiences downtime?
> What is the difference between pirated software and counterfeit software?
> What is the correlation between privacy and confidentiality?
> What are ethics and why are they important to a company?
> What is business intelligence and how can it help a company achieve success?
> What are the causes of dirty data?
> What is the purpose of information cleansing (or scrubbing)?
> How does ETL help transfer data in and out of the data warehouse?
> Watson is an IBM supercomputer that combines artificial intelligence (AI) and sophisticated analytical software for optimal performance as a question answering machine. The supercomputer is named for IBM’s founder, Thomas J. Watson. The Watson supercompu
> What is a data warehouse and why would a business want to implement one?
> What is the difference between a knowledge facilitator and knowledge assets?
> What is the relationship between hackers and viruses?
> What are the positive and negative effects associated with monitoring employees?
> What are the three types of analytics?
> How can a company use disintermediation to achieve a competitive advantage?
> How does system thinking support business operations?
> What type of career are you planning to pursue? How will your specific career use data, information, business intelligence, and knowledge?
> Do you agree that MIS is essential for businesses operating in the information age? Why or why not?
> What is MIS and what role does it plays in an organization?
> Why is it important for a company to operate cross-functionally?
> What is the relationship between data, information, business intelligence, and knowledge?
> How can a manager turn data into information?
> What is data? Why is data important to a business?
> Why are customer relationships important to an organization? Do you agree that every business needs to focus on customers to survive in the information age?
> What is a supply chain inventory visibility system?
> How can a business use clickstream data to help improve website efficiency?
> What are the five primary activities in a supply chain?
> What is supply chain management and why is it important to a company?
> Explain how finding different ways to travel the same road relates to automation, streamlining, and business process reengineering.
> Explain the difference between customer-facing processes and business-facing processes. Which one is more important to an organization?
> Why would a manager need to review an As-Is and To-Be process model?
> Why do managers need to understand business processes? Can you make a correlation between systems thinking and business processes?
> What is an enterprise resource planning system?
> What is a business process and what role does it play in an organization?
> How can a company use Porter’s value chain analysis to measure customer satisfaction?
> What are Porter’s three generic strategies and why would a company want to follow only one?
> What are the four ebusiness advantages?
> How could a company use switching costs to lock in customers and suppliers?

